
by Alicia Motubatse | Oct 15, 2025 | 2025
Massive Discord Breach Leaks Thousands of Government ID Photos In a serious data breach, Discord has confirmed that approximately 70,000 users had their government-issued ID photos exposed after a third-party vendor used for age verification and support services was...

by Alicia Motubatse | Oct 10, 2025 | 2025
Schleswig-Holstein Says Goodbye to Microsoft: A Bold Leap Toward Digital Independence Schleswig-Holstein Pushes for Digital Independence by Ditching Microsoft Tools Schleswig-Holstein, one of Germany’s 16 federal states, has taken a major step in its mission to free...
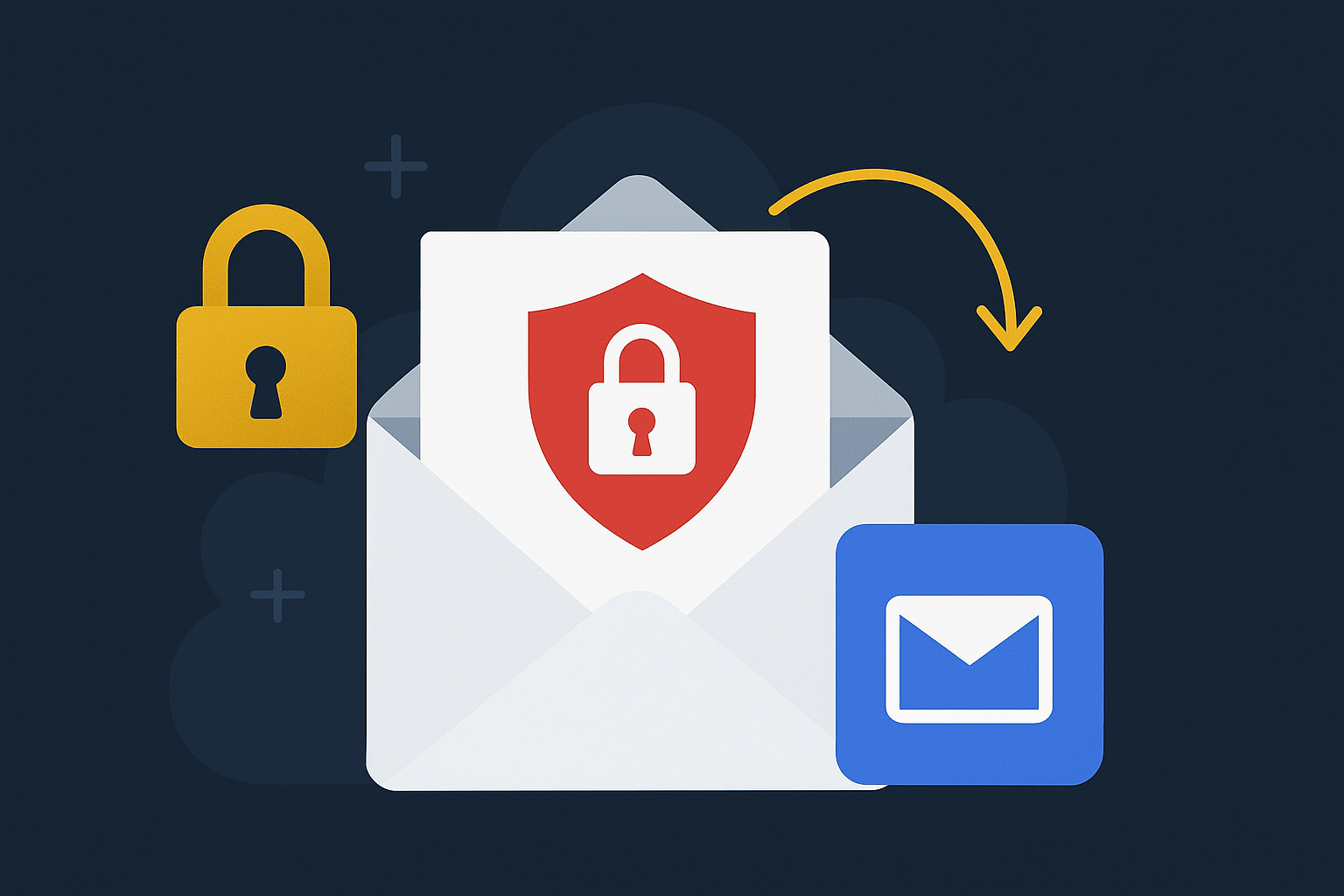
by Alicia Motubatse | Oct 7, 2025 | 2025
Google Expands Email Encryption Across Providers Google is rolling out a major upgrade to Gmail security by enabling end-to-end encryption (E2EE) for emails sent to users on other email platforms, such as Outlook. Previously, this level of encryption was mostly...

by Alicia Motubatse | Oct 3, 2025 | 2025
The PDF Trap: How MatrixPDF Turns Trusted Files into Stealthy Phishing Weapons Cybersecurity researchers at Varonis have uncovered a new phishing method using a toolkit called MatrixPDF, which turns seemingly harmless PDF attachments into powerful delivery tools for...

by Alicia Motubatse | Sep 9, 2025 | 2025
Russia’s ‘Max’ App Aims to Replace WhatsApp Russia is intensifying its control over digital communications by restricting non-Russian apps like WhatsApp and Telegram while promoting its own state-backed “super-app” called Max. Developed by VK (VKontakte),...






