“End-to-end encryption is an essential security tool that helps protect our privacy and security online.” 1
End-to-end encryption (E2EE) is a phrase we hear more and more these days. It has become somewhat of a buzzword in communications, particularly with reference to our common messaging platforms. But what does it really mean and are our daily communications truly encrypted end-to-end?
With our rapid migration to the digital world, the security of our privacy and personal & business information is more important than ever. With the increasing number of cyber-attacks and data breaches, it is essential to take measures to protect our personal information. One such measure is end-to-end encryption (E2EE).
Simply put, as the title would have it, end-to-end encryption is a system of communication that encrypts data from one end of the communication to the other end. The data can only be decrypted by the intended recipient, not by any third-party service or intermediary. In other words, the only people who can access the data are the sender and the recipient.
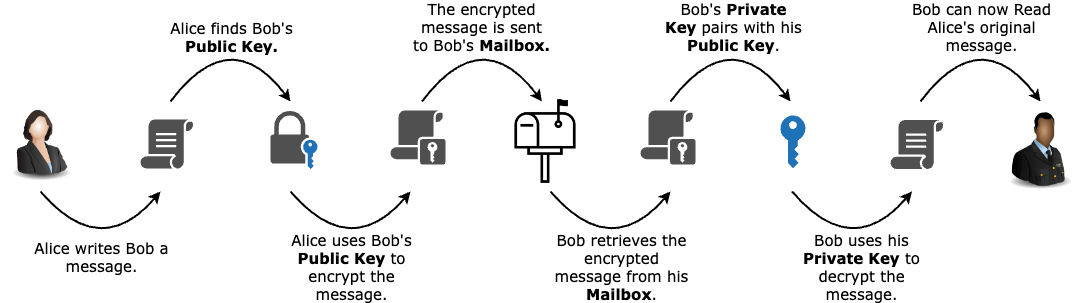
But how does it work? The most common form of end-to-end encryption uses a method called Public & Private Key Infrastructure (PKI). PKI involves the use of two keys, a public key and a private key, for encryption and decryption of data. A user’s public key can be made available to anyone. It can then be used to encrypt messages that are sent to the owner of the corresponding private key. The private key, on the other hand, is kept secret and is used to decrypt messages that were encrypted with its corresponding public key. This can also be referred to as asymmetric encryption.
“End-to-end encryption is like having a locked room where you can keep your confidential information. No one else can access it, not even the service provider.” 2
In this analogy, the letter is like sensitive information being sent over the internet and the public and private keys work together to ensure that only the intended recipient can access and read the information. The public key ensures that anyone can send information securely (the address), while the private key ensures that only the intended recipient can access it. Thanks to Public & Private Key Infrastructure (PKI) we have End-to-End Encryption (E2EE).
E2EE is used in various applications, such as messaging services, email, and online storage. It should be noted that, even though many everyday messaging platforms and apps claim to be end-to-end, purists would disagree3, owing to the fact that a copy of the communication is still stored on the service provider’s platform. True end-to-end means a single version of the correspondence exists, solely between the sender and the recipient. It works by using a unique key for each conversation, which is stored on the devices of the sender and the recipient. When a message is sent, it is encrypted using this key and can only be decrypted using the same key. This ensures that no one else can access the information, even if the data is intercepted during transit. In digital world with frequent security vulnerabilities, end-to-end encryption provides peace of mind, knowing that your communications are protected from prying eyes.
[1] https://www.amnesty.org/en/what-we-do/end-to-end-encryption/
[2] https://www.eff.org/pages/end-to-end-encryption
[3] https://theintercept.com/2016/04/05/why-whatsapps-encryption-is-not-end-to-end/
